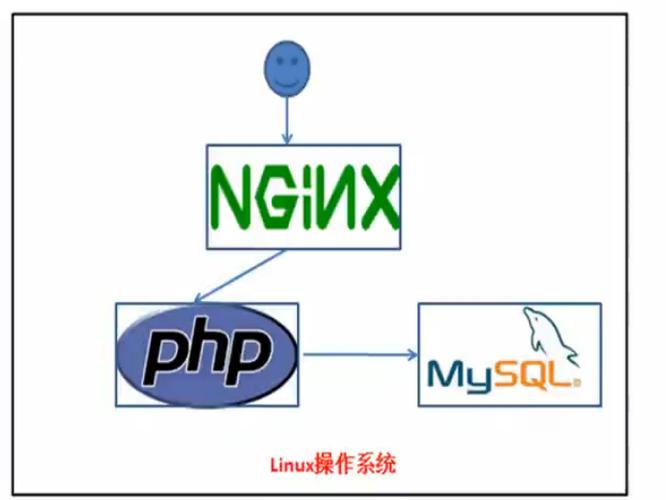
ModSecurity是一个免费、开源的Apache模块,可以充当Web运用防火墙(WAF)。ModSecurity是一个入侵探测与阻挡的引擎.它紧张是用于Web运用程序以是也可以叫做Web运用程序防火墙.ModSecurity的目的是为增强Web运用程序的安全性和保护Web运用程序避免遭受来自已知与未知的攻击。目前已经支持nginx和IIS,合营nginx的灵巧和高效,可以打造成生产级的WAF,是保护和审核web安全的利器。而OWASP是一个安全社区,开拓和掩护着一套免费的运用程序保护规则,这便是所谓OWASP的ModSecurity的核心规则集(即CRS)。我们可以通过ModSecurity手工创建安全过滤器、定义攻击并实现主动的安全输入验证。
作为WAF产品,ModSecurity关注HTTP流量,当发出HTTP要求时,ModSecurity检讨要求的所有部分,如果要求被认为是恶意的,它可以被阻挡、记录或同时记录,这取决于配置。

二、环境准备
OS:CentOS 7.8 x64
测试做事器IP:192.168.168.103
注:系统为最小化安装,支配前已完成系统初始化、内核及安全优化。
三、安装根本依赖文件
1.库文件(yum安装)
rpm -ivh http://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
yum -y install bzip2 bzip2-devel curl curl-devel fontconfig fontconfig-devel freetype freetype-devel gd gd-devel libevent libjpeg libjpeg-devel libpng libpng-devel libvpx libvpx-devel libXpm libXpm-devel libxml2 libxml2-devel perl pcre-devel zlib zlib-devel
2.编译工具——若系统初始化时没有安装则实行
## autoconf
cd /data/tools
wget http://ftp.gnu.org/gnu/autoconf/autoconf-2.71.tar.gz
tar xf autoconf-2.71.tar.gz
cd autoconf-2.71
./configure
make
make install
## automake
cd /data/tools
wget http://ftp.gnu.org/gnu/automake/automake-1.16.3.tar.gz
tar xf automake-1.16.3.tar.gz
cd automake-1.16.3
./configure
make
make install
## libtool
cd /data/tools
wget http://ftp.gnu.org/gnu/libtool/libtool-2.4.6.tar.gz
tar xf libtool-2.4.6.tar.gz
cd libtool-2.4.6
./configure
make
make install
3.扩展软件
## libgd——GD Graphics Library(libgd)是用来动态创建图像的开源图形软件库,紧张用在图像验证码、头像、网络相册等方面,用户利用十分广泛。
cd /data/tools
wget https://github.com/libgd/libgd/releases/download/gd-2.3.2/libgd-2.3.2.tar.gz
tar xf libgd-2.3.2.tar.gz
cd libgd-2.3.2
export PKG_CONFIG_PATH="/usr/local/lib/pkgconfig:${PKG_CONFIG_PATH}"
./configure --with-zlib --with-fontconfig --with-png --with-freetype --with-jpeg
make && make install
cp /usr/local/lib/libgd.so.3.0.10 /lib64/libgd.so.3
## libiconv——基于GNU协议的开源库,紧张是办理多措辞编码处理转换等运用问题由于历史缘故原由,国际化的笔墨常常由于措辞或者国家的缘故原由利用不同的编码。
cd /data/tools
wget http://ftp.gnu.org/pub/gnu/libiconv/libiconv-1.16.tar.gz
tar xf libiconv-1.16.tar.gz
cd libiconv-1.16
./configure
make && make install
## Pcre——Perl库,包括perl兼容的正则表达式库。
cd /data/tools
wget https://ftp.pcre.org/pub/pcre/pcre-8.44.tar.gz
tar xf pcre-8.44.tar.gz
cd pcre-8.44
./configure --prefix=/usr/local/pcre/ --enable-jit --enable-utf --enable-unicode-properties --enable-pcregrep-libz --enable-pcregrep-libbz2 --enable-pcre16 --enable-pcre32
make && make install
## qrencode——二维码天生库(天生和识别):一个用C措辞编写的用来解析二维条形码(QR Code)的程序库,通过手机的CCD摄像头来扫描二维条形码。
cd /data/tools
wget https://fukuchi.org/works/qrencode/qrencode-4.1.1.tar.gz
tar xf qrencode-4.1.1.tar.gz
cd qrencode-4.1.1
./configure --enable-thread-safety
make && make install
cp /usr/local/lib/libqrencode.so.4.1.1 /lib64/libqrencode.so.4
## jemalloc——内存分配器,适宜多线程下的内存分配管理软件。与其它内存分配器比较,它最大的上风在于多线程情形下的高性能以及内存碎片的减少。
cd /data/tools
wget https://github.com/jemalloc/jemalloc/releases/download/5.2.1/jemalloc-5.2.1.tar.bz2
tar xjf jemalloc-5.2.1.tar.bz2
cd jemalloc-5.2.1
./autogen.sh
make && make install
echo '/usr/local/lib' > /etc/ld.so.conf.d/local.conf
ldconfig
四、安装ModSecurity模块
1.安装依赖
yum -y install GeoIP GeoIP-devel git lua lua-devel lmdb lmdb-devel ssdeep-devel ssdeep-libs yajl yajl-devel
## 升级libmaxminddb(https://github.com/maxmind/libmaxminddb/)
YUM安装的libmaxminddb版本为1.2.0,达不到哀求,需升级或安装ModSecurity编译./configure时利用--with-maxmind=no选项将其禁用。本文中卸载掉yum安装的libmaxminddb然夹帐动编译安装需求版本。
yum -y remove libmaxminddb
cd /data/tools
wget https://github.com/maxmind/libmaxminddb/releases/download/1.5.2/libmaxminddb-1.5.2.tar.gz
tar xf libmaxminddb-1.5.2.tar.gz
cd libmaxminddb-1.5.2/
./configure
make && make install
ldconfig
2.安装libmodsecurity
cd /usr/local
git clone --depth 1 -b v3/master --single-branch https://github.com/SpiderLabs/ModSecurity
cd ModSecurity
git submodule init
git submodule update
sh build.sh
./configure --with-lmdb
make && make install
3.安装ModSecurity-nginx(https://github.com/SpiderLabs/ModSecurity-nginx)
cd /usr/local
git clone --depth 1 https://github.com/SpiderLabs/ModSecurity-nginx.git
五、NGINX安装及配置
1.添加组及用户
groupadd -g 1000 www
useradd -s /bin/bash -u 1000 -g www www
2.创建项目及日志目录
mkdir -p /data/logs/nginx
mkdir -p /data/www
cd /data
chown -R www.www www logs
3.下载编译安装Nginx
cd /data/tools/
wget http://nginx.org/download/nginx-1.18.0.tar.gz
tar xf nginx-1.18.0.tar.gz
cd nginx-1.18.0
CFLAGS="$CFLAGS -O3" CXXFLAGS="$CXXFLAGS -O3" ./configure --user=www --group=www --prefix=/usr/local/nginx-1.18.0 --error-log-path=/data/logs/nginx/error.log --lock-path=/usr/local/nginx/var/nginx.lock --with-http_v2_module --with-http_ssl_module --with-http_flv_module --with-http_addition_module --with-http_stub_status_module --with-http_gzip_static_module --with-http_degradation_module --without-http_memcached_module --with-file-aio --with-http_image_filter_module --with-http_realip_module --with-compat --with-threads --with-http_secure_link_module --with-http_dav_module --with-http_mp4_module --with-pcre=/data/tools/pcre-8.44 --with-pcre-jit --with-ld-opt="-ljemalloc" --add-module=/usr/local/ModSecurity-nginx
make 或 make -j2 //2是CPU核心数
make install
cd /usr/local
ln -sf nginx-1.18.0 nginx
注:CFLAGS表示用于C编译器的选项,CXXFLAGS表示用于C++编译器的选项。这两个变量实际上涵盖了编译和汇编两个步骤。
4.添加启动脚本
vi /usr/lib/systemd/system/nginx.service //输入以下内容
[Unit]Description=Nginx - High Performance Web ServerDocumentation=http://nginx.org/en/docs/After=network.target remote-fs.target nss-lookup.target[Service]Type=forkingPIDFILE=/usr/local/nginx/logs/nginx.pidExecStartPre=/usr/local/nginx/sbin/nginx -t -c /usr/local/nginx/conf/nginx.confExecStart=/usr/local/nginx/sbin/nginx -c /usr/local/nginx/conf/nginx.confExecReload=/bin/kill -s HUP $PIDFILEExecStop=/bin/kill -s QUIT $PIDFILEPrivateTmp=true[Install]WantedBy=multi-user.target
chmod a+x /usr/lib/systemd/system/nginx.service
systemctl daemon-reload
## 做事管理
开机启动:systemctl enable nginx.service
开机不启动:systemctl disable nginx.service
启动: systemctl start nginx.service
关闭: systemctl stop nginx.service
重启: systemctl restart nginx.service
查看状态: systemctl status nginx.service
5.修正主配置文件nginx.conf
mkdir -p /usr/local/nginx/conf/vhost
vi /usr/local/nginx/conf/nginx.conf //输入以下内容
user www www;
worker_processes 1;
#worker_processes 2;
#worker_cpu_affinity 0101 1010;
#worker_processes 4;
#worker_cpu_affinity 1000 0100 0010 0001;
#worker_processes 8;
#worker_cpu_affinity 00000001 00000010 00000100 00001000 00010000 00100000 01000000 10000000;
error_log /data/logs/nginx/error.log;
pid /usr/local/nginx/logs/nginx.pid;
worker_rlimit_nofile 65535;
events {
use epoll;
worker_connections 65535;
}
http {
include /usr/local/nginx/conf/mime.types;
default_type application/octet-stream;
log_format json '{"@timestamp":"$time_iso8601",'
'"client":"$remote_addr",'
'"user":"$remote_user",'
'"url":"$request",'
'"status":"$status",'
'"cookie":"$http_cookie",'
'"size":"$body_bytes_sent",'
'"referer":"$http_referer",'
'"useragent":"$http_user_agent",'
'"xforwardedfor":"$http_x_forwarded_for",'
'"requesttime":"$request_time",'
'"upstreamresponsetime":"$upstream_response_time",'
'"upstreamaddr":"$upstream_addr",'
'"upstreamstatus":"$upstream_status",'
'}';
access_log /data/logs/nginx/access.log json;
server_names_hash_bucket_size 128;
client_header_buffer_size 32k;
client_body_buffer_size 128k;
large_client_header_buffers 4 32k;
client_header_timeout 600;
client_body_timeout 1200;
client_max_body_size 2m;
server_tokens off;
sendfile on;
tcp_nopush on;
tcp_nodelay on;
send_timeout 1800;
keepalive_timeout 75;
types_hash_max_size 2048;
###### PHP-FastCGI
fastcgi_connect_timeout 300;
fastcgi_send_timeout 300;
fastcgi_read_timeout 300;
fastcgi_buffer_size 64k;
fastcgi_buffers 8 128k;
fastcgi_busy_buffers_size 128k;
fastcgi_temp_file_write_size 128k;
gzip on;
gzip_min_length 1k;
gzip_buffers 4 16k;
gzip_http_version 1.0;
gzip_comp_level 2;
gzip_types text/plain application/x-javascript text/css application/xml;
gzip_vary on;
include /usr/local/nginx/conf/vhost/.conf;
}
备注:worker_processes、worker_cpu_affinity参数等其他参数可根据实际环境需求进行修正。
5.启动Nginx做事
systemctl start nginx.service
六、测试
1.配置测试站点
cd /data/www
mkdir test
vi test/index.html //输入如下内容
Nginx ModSecurity test!!!
chown -R www.www test
2.配置NGINX虚拟主机文件
vi /usr/local/nginx/conf/vhost/test.conf //输入如下内容
server{ listen 80; server_name 192.168.168.103; root /data/www/test; index index.html index.htm;}
## 重新载入nginx配置
/usr/local/nginx/sbin/nginx -t
/usr/local/nginx/sbin/nginx -s reload
3.测试
仿照攻击,测试未启动ModSecurity时的访问效果,访问URL:http://做事器IP/?<script>alert(“Attack!”)</script>
把稳:若有防火墙的话,放开nginx做事端口;或者关闭防火墙。
效果如下:
七、配置Nginx+ModSecurity-nginx
1.配置modsecurity
mkdir -p /usr/local/nginx/conf/modsecurity/
cd /usr/local/ModSecurity/
cp modsecurity.conf-recommended /usr/local/nginx/conf/modsecurity/modsecurity.conf
cp unicode.mapping /usr/local/nginx/conf/modsecurity/unicode.mapping
2.配置nginx.conf
vi /usr/local/nginx/conf/nginx.conf
在http节点中添加以下内容:
## ModSecuritymodsecurity on;modsecurity_rules_file /usr/local/nginx/conf/modsecurity/modsecurity.conf;
备注:在http节点添加表示全局配置。或在虚机配置文件server节点添加,表示为指定网站配置。
3.下载规则文件及配置
## 下载
cd /data/tools
wget -O coreruleset-3.3.1-rc1.zip https://github.com/coreruleset/coreruleset/archive/v3.3.1-rc1.zip
unzip coreruleset-3.3.1-rc1.zip
cd coreruleset-3.3.1-rc1
## 复制crs-setup.conf.example到/usr/local/nginx/conf/modsecurity/下并重命名为crs-setup.conf
cp crs-setup.conf.example /usr/local/nginx/conf/modsecurity/crs-setup.conf
## 复制rules文件夹到/usr/local/nginx/conf/modsecurity/目录下
cp -r rules /usr/local/nginx/conf/modsecurity/
## 修正规则文件名称,去掉 .example
cd /usr/local/nginx/conf/modsecurity/rules
mv REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf
mv RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf
4.配置modsecurity.conf
vi /usr/local/nginx/conf/modsecurity/modsecurity.conf
## 将SecRuleEngine DetectionOnly 改为 SecRuleEngine On
#SecRuleEngine DetectionOnlySecRuleEngine On
## 确保ModSecurity在记录审计日志时保存要求体IJ 改为 C
#SecAuditLogParts ABIJDEFHZSecAuditLogParts ABCDEFHZ
## 在文件末端添加以下内容:
Include /usr/local/nginx/conf/modsecurity/crs-setup.confInclude /usr/local/nginx/conf/modsecurity/rules/.conf
八、重新加载Nginx并测试效果
1.重新载入nginx配置
/usr/local/nginx/sbin/nginx -t
/usr/local/nginx/sbin/nginx -s reload
2.测试
仿照攻击,访问URL:http://192.168.168.103/?<script>alert(“Attack!”)</script>
效果如下: